SAML SSO
Overview
Dust supports SAML Single Sign-On (SSO) to manage your team's access to our platform securely and effortlessly using your existing Identity Provider (IdP). This feature simplifies user management and enhances security by centralizing authentication.
Supported Identity ProvidersWhile this guide focuses on generic SAML configuration, Dust works seamlessly with all major SAML-compliant Identity Providers including:
- Okta
- Azure AD
- Google Workspace
- OneLogin
Setting up SAML Single Sign-On (SSO)
To enable SSO for Dust using SAML, follow these steps to create a custom app integration in your Identity Provider (IdP).
1. Identify an Admin:
Choose an admin with comprehensive access to both your IdP admin dashboard and Dust admin. This is necessary as enabling SAML SSO requires creating a custom integration in your IdP.
2. Get Your Dust SAML Configuration Values
- In Dust, navigate to Admin > People & Security > Single Sign-On > Activate Single Sign-On
- You'll find all the necessary SAML configuration values that you'll need to set up your IdP:
- ACS (Assertion Consumer Service) URL
- Entity ID / Audience URI
Keep this page open as you'll need these values in the next step.
3. Create a Custom App Integration in your IdP
- Navigate to your IdP's admin dashboard and locate the section for creating new applications or integrations.
- Select SAML 2.0 as the protocol when creating a new application.
- Configure the following SAML settings using the values from Dust:
- Application Name: Enter "Dust" as the app name
- ACS (Assertion Consumer Service) URL: Copy from Dust
- Entity ID / Audience URI: Copy from Dust
- Logo: You can find our logo here.
Keep your IdP configuration page openYou'll need to copy several pieces of information for the next step:
- IdP Single Sign-On URL
- IdP Entity ID
- X.509 Certificate
SAML Attributes Configuration
The following SAML attributes must be properly configured in your IdP for successful login.
All attributes are required to ensure that the SSO connection is functional
Make sure that the admin setting up the connection has these fields populated to complete the process
Even if EntraID does not require all fields, users must have values in these fields in order to be able to SSO into Dust.
Required SAML Attributes
-
Email
- Claim name:
email - Schema URI:
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier - Used for user identification and authentication
- Must match the user's email address
- Claim name:
-
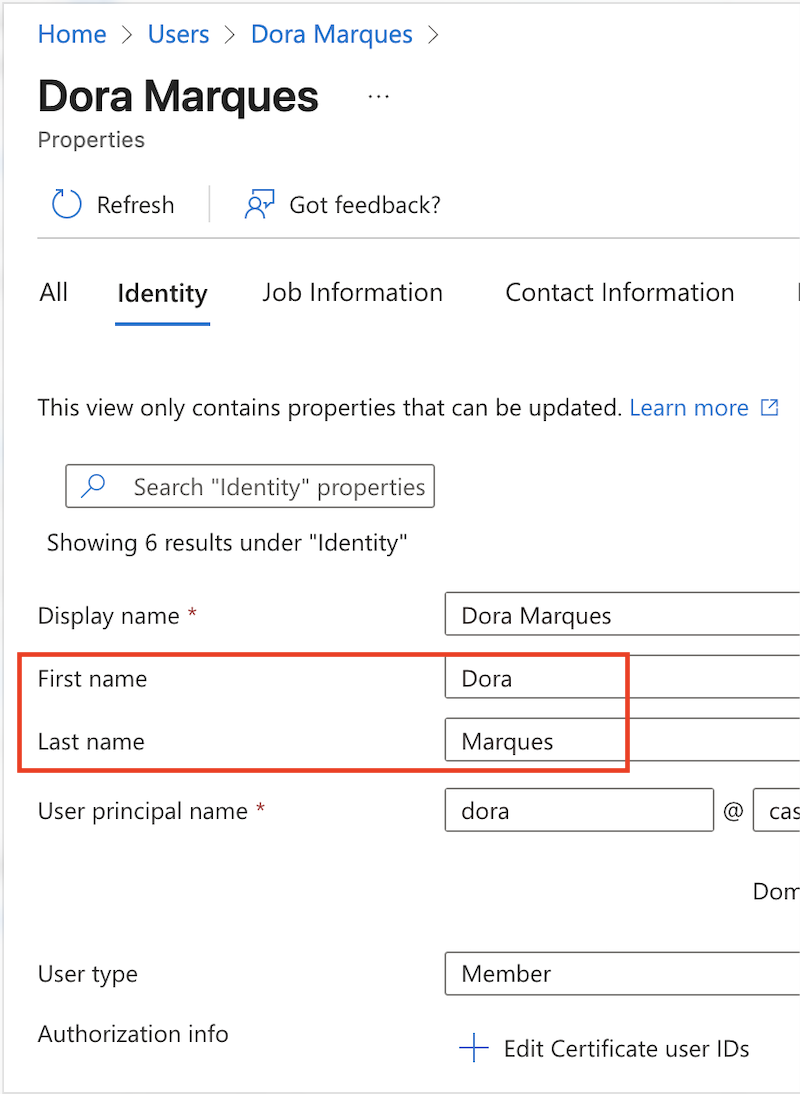
First Name
- Claim name:
given_name - Accepted Schema URIs (any of the following):
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givennamehttp://schemas.xmlsoap.org/ws/2005/05/identity/claims/name
- Sets the user's first name in Dust
- Claim name:
-
Last Name
- Claim name:
family_name - Schema URI:
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname - Sets the user's last name in Dust
- Claim name:
-
Email verified
- Claim name:
email_verified - Schema URI:
true - Mark the user's email has verified. Required to have existing identities merging.
- Claim name:
Attribute Mapping ReferenceFor IdP administrators, here's the complete attribute mapping schema in JSON format:
{ "email": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", "given_name": [ "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname", "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name" ], "family_name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname", "email_verified": true }
Google Workspace SAMLWhen setting up a SAML app in Google Workspace 📘, it is not possible to set the
email_verifiedclaim totrue. This is a known issue in the Auth0 community, which can be bypassed by mapping a dynamic field such asnameidentifierto theemail_verifiedfield
4. Enabling SAML Single Sign-On (SSO) in Dust
- Return to the Dust SSO configuration page (Admin > People & Security > Single Sign-On > Activate Single Sign-On)
- Enter the following details from your IdP setup:
- IdP Single Sign-On URL
- X.509 Certificate
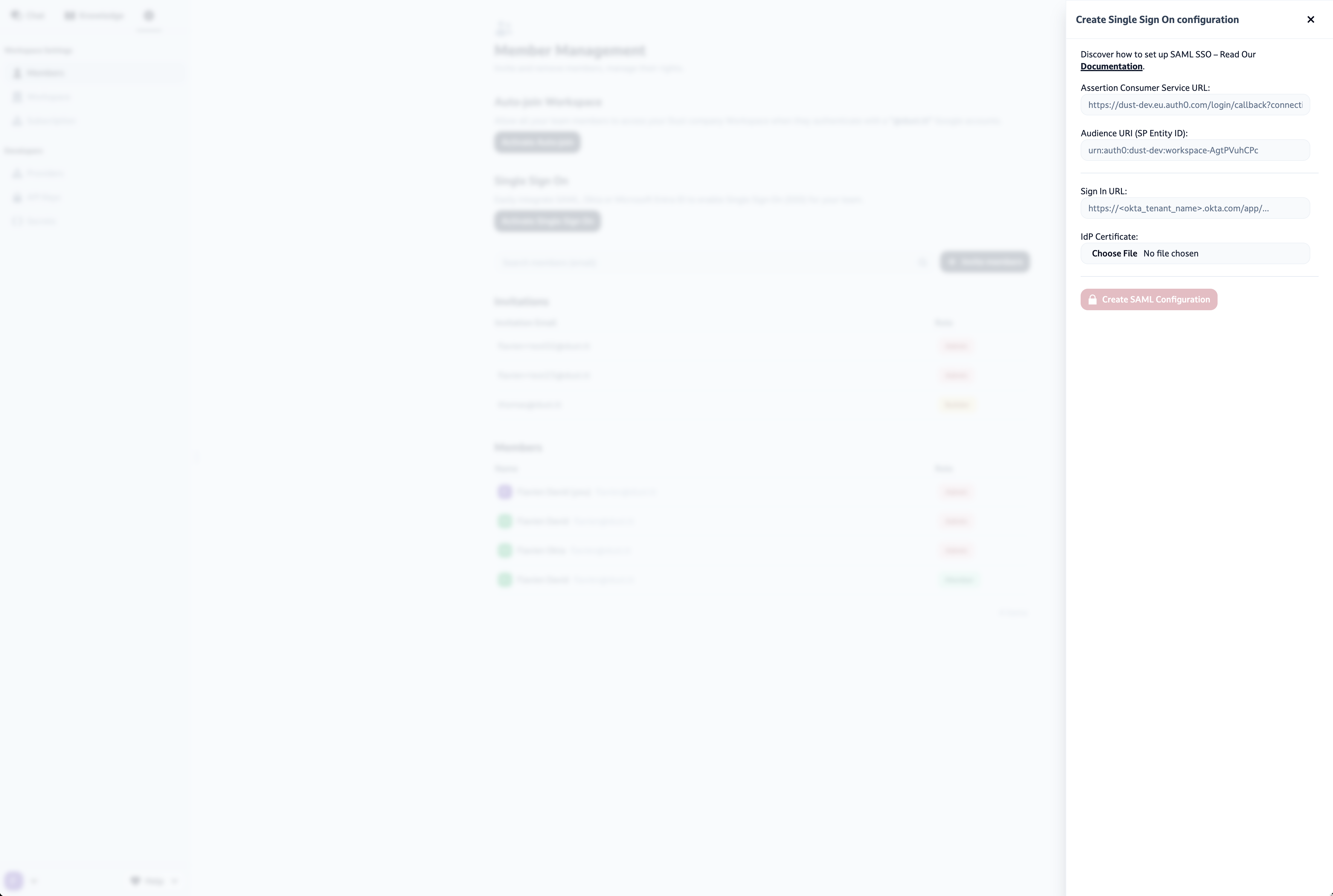
Once you've entered this information, click on Create SAML Configuration. SAML SSO is now enabled on your workspace.
If Auto-join Workspace is enabled, all members attempting to log in to Dust using their enterprise email addresses will be automatically redirected to your IdP for authentication.
5. Enforcing SAML Single Sign-On (SSO) in Dust
After enabling SSO, you have the option to enforce it across the entire workspace. This means that users will no longer be able to log in using their social media accounts. Please note that enabling this setting will log out all users who are not currently using SAML, and they will be required to log back in using their IdP credentials.
6. Using IdP-initiated flows rather than SP-initiated flows (optional)
By default, only SP-initiated flows are allowed on Dust's side. However, if your company is using IdP-initiated flows for convenience, despite the known security flaws, Dust can support this way of authenticating.
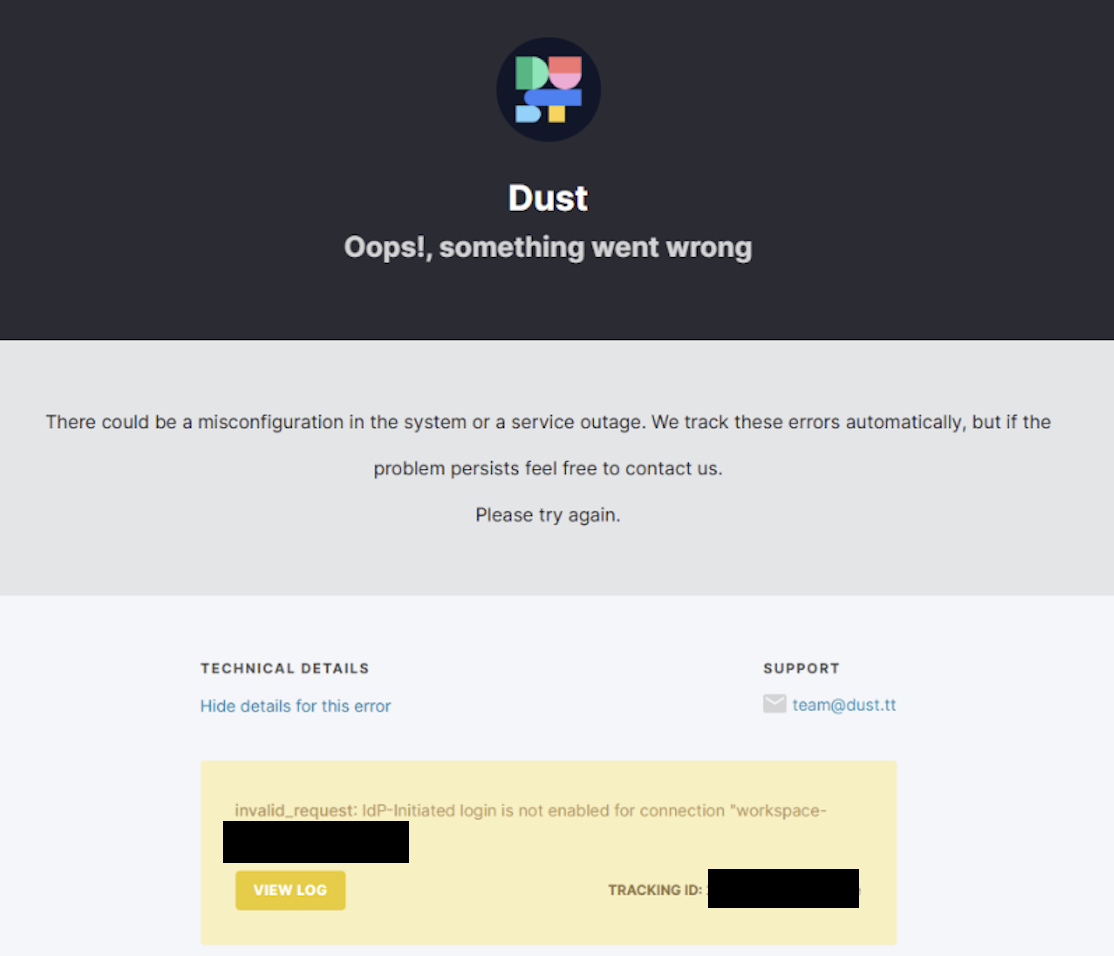
Warning on IdP-initiated flowsIf your company is allowing IdP-initiated flows, the message displayed in Dust will be "invalid_request: IdP-initiated login is not enabled for connection "workspace- not enabled "
To enable IdP-initiated flows for your Dust SSO integration, you'll need to:
- Contact Dust support to request enabling IdP-initiated login for your specific SSO connection
- Confirm that you understand and accept the security implications of enabling IdP-initiated flows
The support team will be able to enable this feature for your SSO connection.
Updated 25 days ago